April 22, 2025
Ransomware Gangs Take Down Rivals, Exploiting their Shoddy AI Coding
In the shadowy corners of the dark web, ransomware groups are proving that there’s no honor among thieves. The latest trend in this criminal underworld is an escalating turf war, with experienced ransomware gangs hacking and taking over rival operations. These hostile takeovers are not just about flexing technical muscle; they’re part of a calculated strategy to dominate the market and attract more affiliates. The most brazen player in this game? A group calling itself DragonForce, which has been systematically dismantling competitors and absorbing their operations.
This new wave of attacks reveals a surprising vulnerability: many of these ransomware groups rely on unsophisticated, AI-generated code, leaving them wide open to exploitation. For all their bluster about technical prowess, some of the biggest names in ransomware—like RansomHub and BlackLock—have been caught flat-footed, exposing cracks in their operations that more experienced groups are now exploiting.
Looking to stay ahead of dark web threats? Get the latest in dark web news, OSINT tools, and more when you subscribe to the DarkBlue newsletter.
The franchise model of cybercrime
Ransomware isn’t just about locking up files and demanding payment anymore. The real money lies in what can only be described as a franchise model. Leading ransomware groups operate like corporations, recruiting affiliates who carry out attacks in exchange for a cut of the profits. This model allows them to scale rapidly while maintaining dominance in the market.
To grow their networks, these groups need to attract affiliates—and nothing says “join us” like a show of dominance over rivals. In recent months, this has led to an emerging trend: ransomware gangs attacking each other. By hacking into rival sites, defacing their homepages with calling cards, and sometimes outright taking over their operations, these groups are sending a clear message to potential recruits: we’re the ones in charge.
DragonForce has taken this strategy to new heights. In a series of high-profile attacks, the group has targeted two prominent rivals—BlackLock and RansomHub—and claimed their sites as subsidiaries.
DragonForce’s hostile takeovers
BlackLock was one of the first victims of DragonForce’s aggressive expansion campaign. BlackLock had already been making waves by splitting its operation into three subgroups—El Dorado, Momona, and BlackLock itself—in an effort to capture more market share. But this strategy backfired spectacularly when DragonForce hacked into all three groups’ onion sites on the dark web, defaced them with its logo, and took control of their operations.
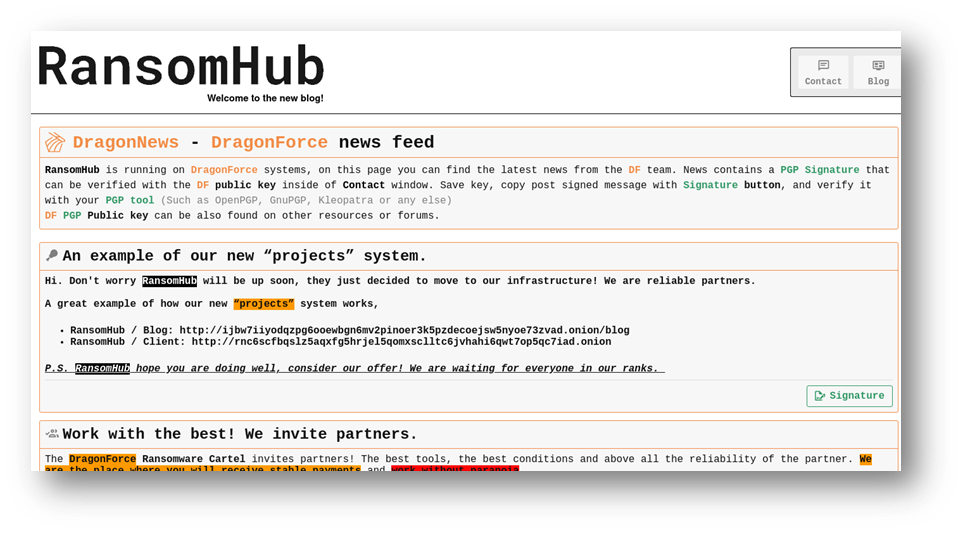
Figure 1: RansomHub displaying the DragonForce logo and name on its news feed after DragonForce's hostile takeover, as captured in DarkPursuit
RansomHub was next on DragonForce’s hit list. Until recently, RansomHub was considered one of the fastest-growing ransomware operations on the dark web—a name that appeared on nearly every top 10 list in the industry. But even this powerhouse couldn’t withstand DragonForce’s assault. In a move that shocked observers, DragonForce hacked into RansomHub’s infrastructure, took over its site, and began running it as if it were their own business unit.
These takeovers aren’t just symbolic victories; they’re strategic moves designed to eliminate competition and consolidate power in the ransomware ecosystem.
AI code: A double-edged sword
One of the most striking aspects of these attacks is how they’ve exploited weaknesses in AI-generated code. Many newer ransomware groups have turned to artificial intelligence to streamline their operations, using AI tools to write malicious code quickly and at scale. But while this approach might save time and resources, it comes with significant risks. AI-generated code often lacks sophistication and robust operational security (opsec), making it easier for more experienced hackers to exploit.
Both BlackLock and RansomHub relied heavily on AI-assisted coding—a fact that DragonForce was quick to take advantage of. By identifying vulnerabilities in their rivals’ codebases, DragonForce was able to breach their systems with relative ease. It’s a stark reminder that even in the world of cybercrime, cutting corners can have dire consequences.
This isn’t an isolated phenomenon. Other ransomware groups have also fallen victim to similar tactics recently. Ransomware gang Everest’s site was taken down by a hacker in early April. A message was posted to their homepage that read, “Don’t do crime CRIME IS BAD xoxo from Prague,” and the site was taken offline a few days later. The success of these many attacks underscores just how vulnerable some of these operations are due to being built on shaky technical foundations.
A shifting landscape
The rise of ransomware-on-ransomware attacks is just one part of a broader shift in the cybercrime landscape. Another notable trend is the move away from traditional ransom demands altogether. Hunters International, one of the first groups to adopt this approach, now focuses solely on stealing data and selling it on underground markets rather than threatening to lock or delete it.
This shift is likely a reaction to declining ransom payments; reports indicate that payouts have dropped by 35% as more victims refuse to pay or find alternative ways to recover their data. For groups like Hunters International, selling stolen data directly is proving to be a more reliable revenue stream.
The future of cybersecurity: monitoring the dark web
As cybercrime continues to escalate at unprecedented levels, powered by AI and supported by nation-states, cybersecurity professionals must adapt to meet the growing threat. Ransomware and digital extortion are no longer just a nuisance for businesses but a global crisis with far-reaching implications for national security, economic stability, and personal privacy.
Organizations can stay ahead of these evolving threats by leveraging platforms like the DarkBlue Intelligence Suite. With its AI-enhanced dark web search capabilities, real-time keyword monitoring, and integration with open source dark web monitoring tools like OSINT platforms, DarkBlue offers unparalleled insights into hidden criminal activities. Its secure environment allows investigators to explore dark web tools without exposing themselves to risk while streamlining workflows through integrated case management features. Request a free trial to test out DarkBlue today.
As ransomware evolves, so too must the strategies to counter it—making vigilant monitoring of dark web activities and innovative defense mechanisms critical to the fight against cybercrime in 2025 and beyond. Organizations should consider leveraging platforms like DarkBlue Intelligence Suite to enhance their threat intelligence capabilities, monitor emerging cyber threats, and stay ahead of ransomware groups operating in the shadows.