June 26, 2025
What is the Dark Web (and How Do I Get on It)?
For most people, hearing “dark web” conjures an image of a hacker in a mask and hoodie, running incomprehensible lines of code on their computer like something out of The Matrix. The dark web seems like a completely foreign and inaccessible place, one that’s hard to find and that you’d only go to if you were looking to do something illegal.
The truth is, some of those stereotypes aren’t far off. But the dark web is surprisingly easy to access, and there are some legitimate uses for its heightened anonymity features. Plus, it’s a great place for the good guys to get intel and track down criminals…if it’s accessed safely, with all necessary precautions.
In this article, we’ll look at:
- The definition of the dark web (and how it’s different from the open and deep web)
- What’s on the dark web (and who goes there)
- How you too can access the dark web (and stay safe doing it)
Keep reading to learn more!
Looking to stay informed about the dark web? Get the latest in dark web news, OSINT tools, and more when you subscribe to the DarkBlue newsletter.
What exactly is the dark web?
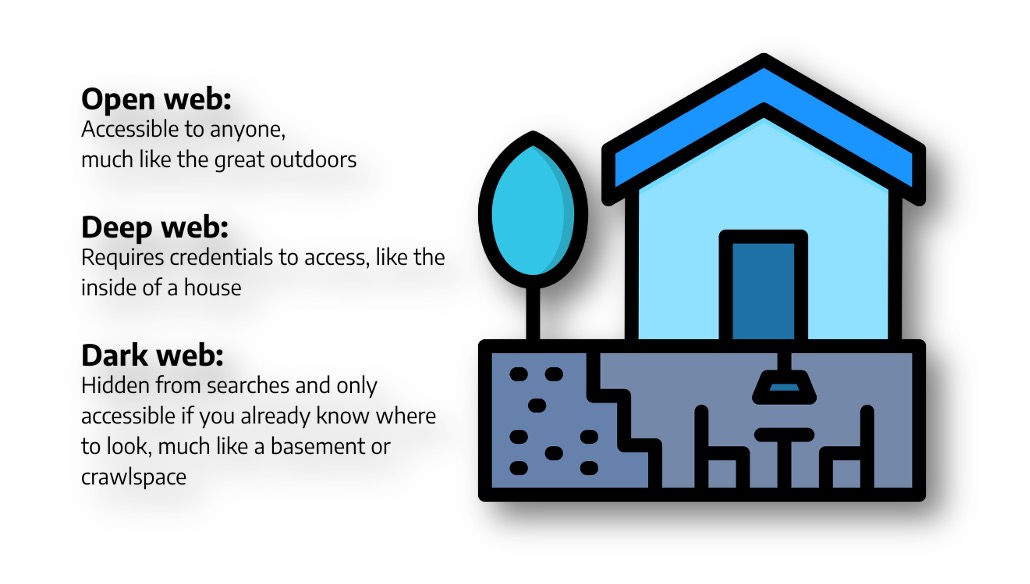
In the simplest of terms, both deep and the dark web are a subset of sites on the internet that are not indexed for traditional search engines. Dark web sites also have an added layer of anonymity because they must be accessed using specialized software, like Tor.
Let’s break that down a bit.
The open web sites you and I use every day are “indexed.” This means they are part of a massive list of sites that traditional search engines like Google and Bing reference every time you search. When you type in something like “banks in Nebraska” or “news,” search engines are able to quickly scan the full indexed list to provide you with the specific URLs that let you access the sites, such as “https://www.ne.bank” or “https://www.cnn.com.”
Tip: You’ll also see the open web also referred to as the “clear net” or “surface web.”

Figure 1: Example of an open web search engine returning indexed site results
That’s all pretty straightforward. However, people often don’t realize that they also use the deep web every day. That’s because any time you provide credentials to log into a site–like to access your email, Netflix account, or banking information–all pages beyond the initial login page are unindexed. You wouldn’t want people to be able to return search results that included the contents of your private emails or your complete bank account number, right? For that reason, only the homepages of these sites are indexed on the open web. Everything beyond a paywall or login screen is hidden from searches, making it part of the “deep web.”
Of course, the dark web takes things a step further. Whereas you can typically find the homepages of deep web sites by searching (you just have to log in to access the rest), even dark web homepages are anonymized and unindexed. They typically include a random string of numbers and letters to make them impossible to guess. For example, as of today, the URL for the most popular forum on the dark web, Dread, is dreadytofatroptsdj6io7l3xptbet6onoyno2yv7jicoxknyazubrad[.]onion. Pretty hard to stumble across that if you don’t already have the exact address, right? Plus, site onions are constantly changing, so the URL for Dread may already be different by the time you’re reading this.
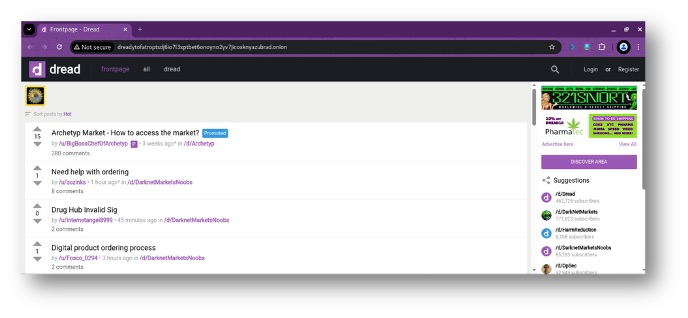
Figure 2: Dread, a popular dark web forum, as captured in DarkPursuit
Therefore, “knowing someone,” such as a contact you met on another dark web forum, becomes highly valuable to help you gain access to any particular dark web site. While there are a few dark web search engines and link directories, such as Ahmia and Deep Search, they work by crawling dark web sites rather than referencing an index, which makes them incomplete and sometimes unreliable. Furthermore, they require a dark web browser, and accessing the dark web directly from your computer carries inherent risk.
Speaking of specialized software, another wrinkle to the equation is that you typically need a specific type of browser to access dark web sites. Try opening a dark web URL in Chrome, and it will return an error. These specialized browsers have built-in anonymity features that help conceal the identity of the user and make them difficult to track.
For example, you’ve probably heard of Tor, the most famous and by far the most used dark web browser. (Hint, all of its site URLs end in .onion instead of .com.) Tor works by encrypting and routing your internet traffic through a series of servers, masking your IP address and location.
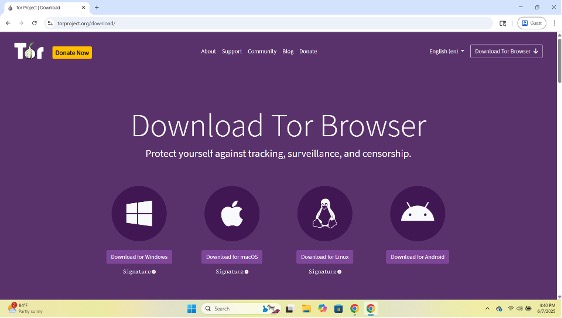
Figure 3: Tor download available in a Chrome browser
While you do need a special browser to access the dark web, it may surprise people to learn that no special hardware or technical skills are required. If you wanted to, you could type “download Tor” into your Safari or Chrome search bar right now, install Tor, and get on the dark web within minutes (not that we advise doing so until you’ve at least read section three about how to stay safe). Other, less popular dark web browsers include I2P, FreeNet/HyphaNet, and ZeroNet, which can also be downloaded from the open web.
Got all that?
So, to recap, anything available to everyone via search is part of the open web, while any page behind credentials is part of the deep web and not available to search engines. Dark web sites also don’t show up in searches, plus they require special browsers to access them. You typically need someone to give you the exact dark web URL in order to find a site.
Tip: While these browsers provide anonymity, that doesn’t mean they keep you safe. There are plenty of malware and cyber attack tools on the dark web aimed at gaining access to your computer and learning everything there is to know about you. So, while dark web browsers do help you hide certain identifying information that open web browsers don’t, for total peace of mind it is highly advised that you access dark web browsers via specialized virtual machines like DarkPursuit that protect you from exposure. (We’ll cover this more in depth later.)
So, who uses the dark web, and for what?
Hint: Not many fine, upstanding citizens
Sure, there are a few privacy-focused reasons that people might use the dark web for non-nefarious reasons. Journalists, whistleblowers, and citizens in authoritarian countries sometimes use dark web resources to communicate securely and avoid surveillance. After all, the dark web was invented by the U.S. military as a way of securely communicating in countries with strict internet censorship. Several privacy advocacy groups continue to host platforms on the dark web to provide safe, anonymous access to information.
However, the high level of anonymity afforded by the dark web also unfortunately leads to a significant amount of criminal activity. Here are a few common uses for dark web sites:
- Drug trafficking: Everything from fentanyl to semaglutides like Ozempic is available on darknet drug markets, much of it shipped from China and distributed to the U.S. via Mexican cartels
- Ransomware and ransomware-as-a-service (RaaS): Hacking is big, and holding data for ransom from groups like government organizations, hospitals, schools, and private companies has skyrocketed in recent years, although some sites prefer to simply sell you their ransomware tools or services
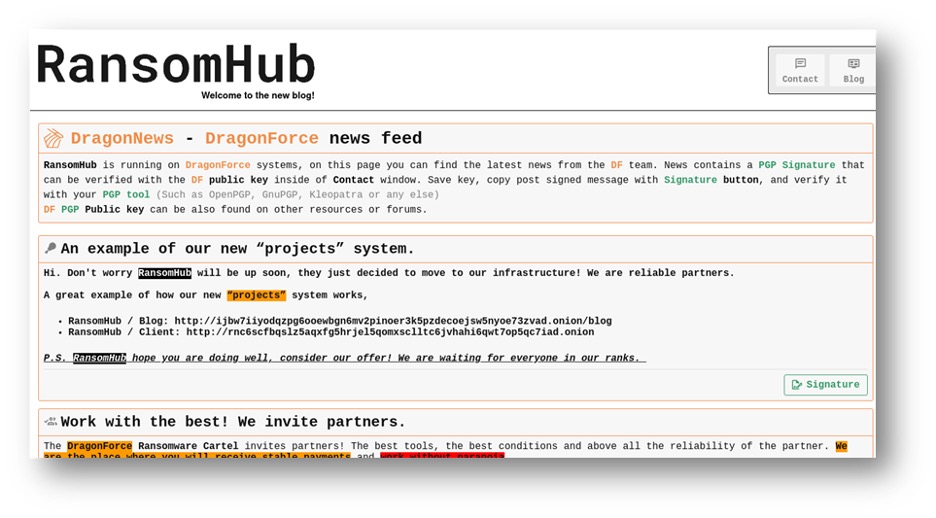
Figure 4: RansomHub, a popular ransomware dark web site, as captured in DarkPursuit
- Fraud: Fueled by AI scripts and vibe coding, there’s been an alarming increase in investment scams like Romance Baiting (aka Pig Butchering), crypto drainers, highly sophisticated malware, and social engineering and spear phishing at scale
- Nation-state activity: State-sponsored groups like North Korea’s Lazarus Group and numerous ransomware gangs backed by China and Russia use DDoS attacks and other malware tools to engage in anti-Western activism and propaganda, destabilizing institutions and leaking data, as well as spreading disinformation and distrust
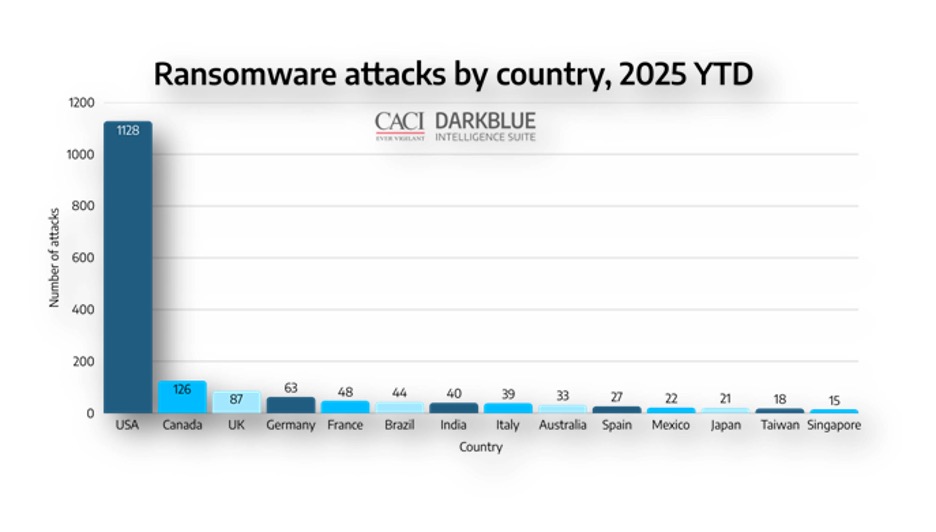
- Extremist violence: Groups like 764 and Harm Nation leverage dark web and cybercrime tools to commit violent crimes, while violent extremist organizations like cartels, Al-Qaeda, and the Islamic State leverage the dark web for communication and propagation, fundraising and financial transactions (including Bitcoin donations), and online extortion
- Human trafficking and CSAM: Child Sexual Abuse Material (CSAM) is widely propagated and sold on the dark web, as well as child and adult human trafficking
Nearly all of the above criminal activities involve cryptocurrency as a means of paying for illicit goods and services on dark web markets.
While Bitcoin is still the most common due to its ease of use, Monero is becoming increasingly popular on dark net markets due to its enhanced privacy features that make transactions more difficult to trace. New coins also pop up frequently, often designed specifically for fraud and scams, such as rug pulls and pump and dump schemes. There are also a high number of cryptocurrency mixers (also known as tumblers) meant to help people obscure attribution of their transactions (essentially money laundering), and there is a strong preference for crypto exchanges that side-step KYC (Know Your Customer) regulations.
Using the dark web for intelligence and security
So, in short, the dark web is indeed a hotbed for all kinds of criminal activity. However, this also makes it a great source of intel. That’s why you’ll find plenty of analysts and investigators also accessing the dark web in order to track down those doing harm and bring them to justice.
For organizations responsible for public safety, national security, and financial oversight, the dark web is a critical source of open-source intelligence (OSINT). While it’s hidden, it is “open” in the sense that the information is publicly accessible without needing a warrant—if you know where and how to look safely.
Examples of intelligence value from the dark web:
- Federal and defense agencies track fentanyl distribution, monitor ransomware leaks, and identify threats to public officials.
- State and local law enforcement use dark web intel to map drug networks, identify child exploitation operations, and detect active threats.
- Financial institutions monitor for stolen credentials, compromised accounts, or discussions of laundering tactics to enhance their AML and fraud response.
- Executive protection and investigative firms use dark web monitoring to detect doxxing, threats to corporate leadership, or exposed PII related to clients
How can I use the dark web safely?
Great question! Considering all the nation-state activity, hacking, and malware services and tools available on the dark web, it isn’t a place you want to access without taking proper precautions. Also, given the high amount of violent extremism and CSAM, there is an inherent risk of accidentally viewing harmful imagery that can stay with you for a long while.
Best practice when accessing the dark web is to do so through a virtual machine. This protects your computer from attacks and masks your IP, making it nearly impossible for bad actors on the dark web to pinpoint your location or gain access to your data and device. One great option is DarkPursuit, a secure live access tool that lets you access dark web browsers and multiple AWS open web regions without fear of malware or exposure. DarkPursuit also has built-in evidence gathering features and options for content safety that let you blur images and mute sound while on the live dark web.
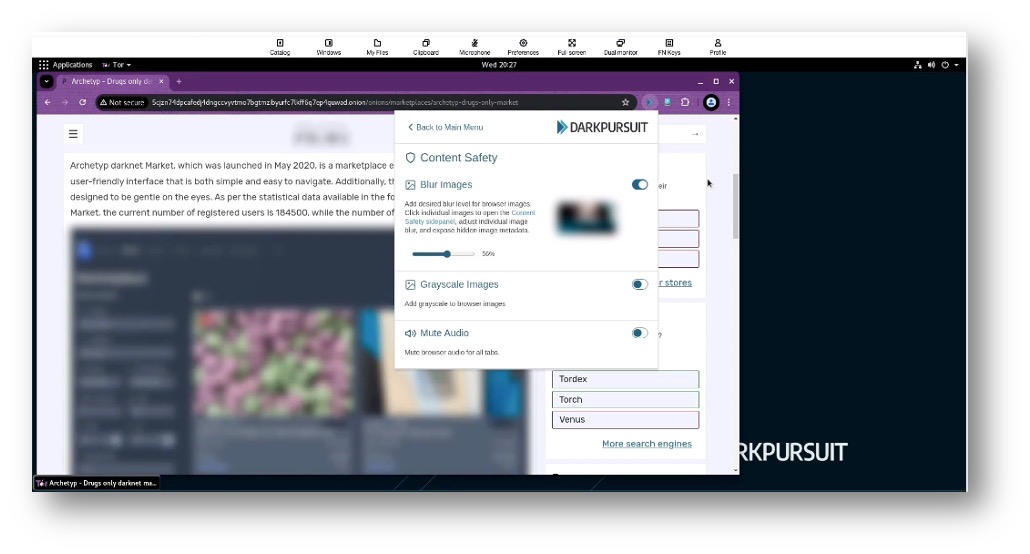
Figure 5: Image blur feature in DarkPursuit
However, if a virtual machine isn’t an option, there are steps you can take to stay safe. The single most important one is to never click on a link or download a file from the dark web. You have no idea what might be sneaking through, and you could easily enable surveillance or even remote control access of your computer, putting yourself and any operations you might be conducting at risk.
Regardless of whether you use a virtual machine, it’s also important to conceal your identity. Never use an email address for a dark web profile that is associated with your personal or work accounts. It’s advisable to create a new email address, such as a ProtonMail address, just for your dark web use. Also, never reuse usernames from other sites or social media associated with you, and ensure any usernames you create do not have identifying references in them.
Learn more tips and techniques for safe and effective intelligence gathering on the dark web in our article, “Dominate Dark Web Data Collection.”
But access isn’t enough—analysis is key
While it’s important to be safe when accessing the dark web, simply getting on Tor will not magically enable you to locate and ID the bad guys. As mentioned earlier, navigating the dark web can be a challenge in and of itself due to its anonymized structure, to say nothing of tracing a threat actor back to a real-life name and address. To effectively operate on the dark web, analysts must navigate thousands of hidden sites, accurately interpret threat actor language and tradecraft, and connect dots across aliases, platforms, and cryptocurrency transactions.
That’s where tools like the DarkBlue Intelligence Suite come in. DarkBlue is designed to make it easy to find the information you need, then empower analysts and investigators to safely track threat actors onto the live dark web.
DarkBlue regularly scrapes dark web sites, copying their data and ingesting it into a single, searchable database. This allows analysts and investigators to enter search terms just like you would on the open web and quickly pull back relevant sites, even hidden dark web ones.
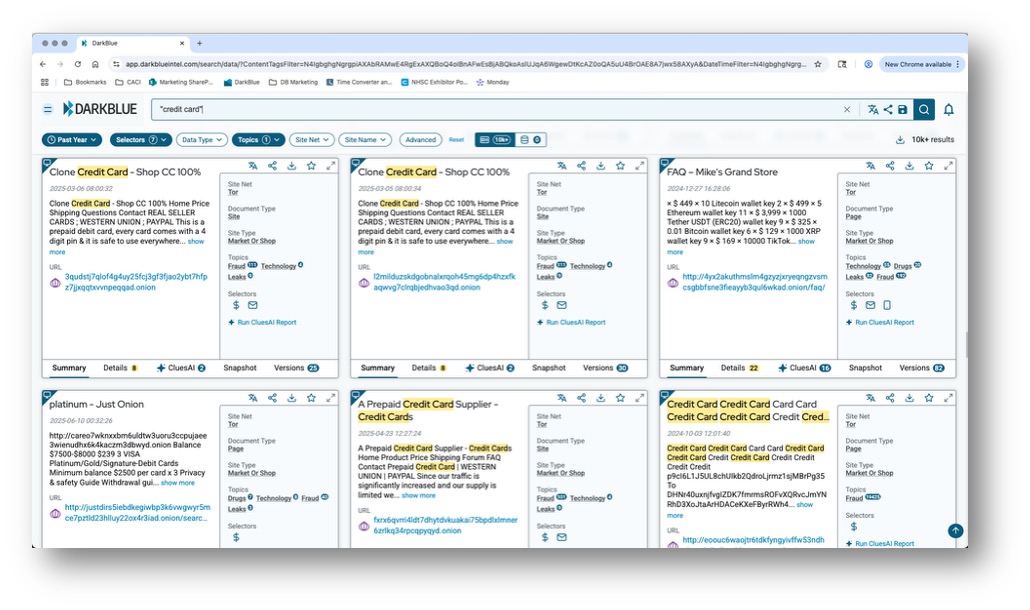
Figure 6: Search results in DarkBlue
DarkBlue’s CluesAI tool saves you time by generating automated intelligence reports for running down leads and deanonymizing bad guys. CluesAI works by scanning relevant records and revealing relationships between data points like usernames, contact information, cryptocurrency wallets, and more.
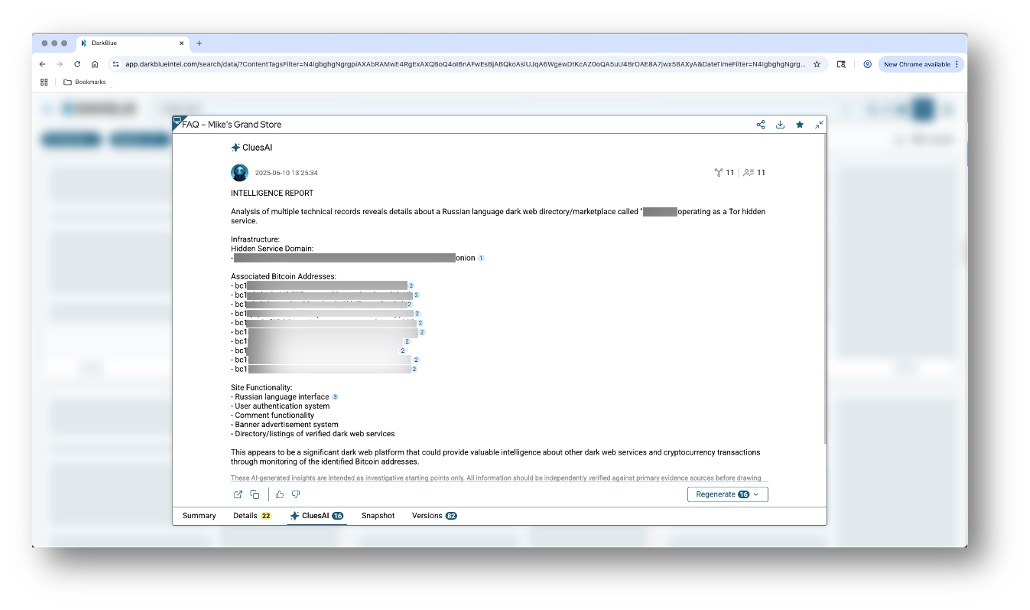
Figure 7: CluesAI report in DarkBlue
Do more in one tool by viewing recent Bitcoin activity for any bitcoin wallets uncovered, and safely pursue threat actors onto the live dark web with DarkBlue’s managed attribution tool, DarkPursuit.
Final thoughts
The dark web has a bad reputation–and it comes by that reputation honestly. But that doesn’t mean it’s impossible to find and take down the bad guys. U.S. law enforcement and international partners have made several very high-profile seizures and arrests in recent months, proving that nobody stays anonymous forever. The more your team understands what’s out there—and how to access it responsibly—the more effective you can be in identifying threats, protecting people, and stopping harm before it reaches the surface.
If your mission depends on timely, credible, and safe dark web intelligence, it’s time to integrate dark web OSINT into your workflow.
Want to stay ahead of dark web threats? Sign up for the DarkBlue newsletter or request a free trial to see how safe, fast, and scalable dark web investigations can be.