April 24, 2025
Inside Garantex: The Sanctioned Crypto Hub Fueling Illicit Finance
On March 7, 2025, a coordinated international operation led by the U.S. Secret Service, in partnership with German and Finnish authorities, delivered what should have been a death blow to Garantex, a notorious cryptocurrency exchange operating out of Russia. Garantex had long been a hub for money laundering, ransomware payments, and even terrorist financing, processing at least $96 billion in cryptocurrency transactions since its inception in April 2019. Yet, in a stunning display of resilience—and audacity—the exchange was back online within just days of its takedown.
Looking to stay ahead of dark web threats? Get the latest in dark web news, OSINT tools, and more when you subscribe to the DarkBlue newsletter.
The coordinated takedown
The operation against Garantex was broad and meticulous. U.S. authorities seized three domain names tied to the exchange—Garantex.org, Garantex.io, and Garantex.academy—while German and Finnish law enforcement confiscated servers hosting its operations. Additionally, over $26 million in laundered funds were frozen. Two key administrators, Aleksej Besciokov and Aleksandr Mira Serda, were indicted on charges including money laundering conspiracy and sanctions violations. If convicted, they face decades in prison.
Prior to this, the exchange had already been sanctioned by the U.S. Treasury’s Office of Foreign Assets Control (OFAC) in 2022 for facilitating over $100 million in illicit transactions. It had evaded detection by frequently moving its operational wallets to new addresses—a tactic that allowed it to continue thriving even under scrutiny.
A rapid resurrection
Despite the speed and thoroughness authorities exercised taking down Garantex, within days of the seizure a coordinated rebrand called “Grinex” had emerged, with a brazen strategy to recover its customer base.
The Grinex website bears striking similarities to Garantex’s original platform, and reports suggest that Grinex was operationally prepared months before Garantex’s takedown, with domains registered and email systems configured well in advance. Blockchain analytics firms have traced liquidity transfers from Garantex wallets to Grinex accounts, including $60 million worth of ruble-backed stablecoins known as A7A5. These funds were systematically burned and re-minted to erase transaction histories—a sophisticated laundering technique designed to thwart regulatory scrutiny.
Using a Telegram channel, the remaining Garantex administrators began contacting users whose funds were frozen during the seizure. Customers were instructed to travel to one of several Russian cities for in-person meetings with administrators to verify their identities and reclaim their funds.
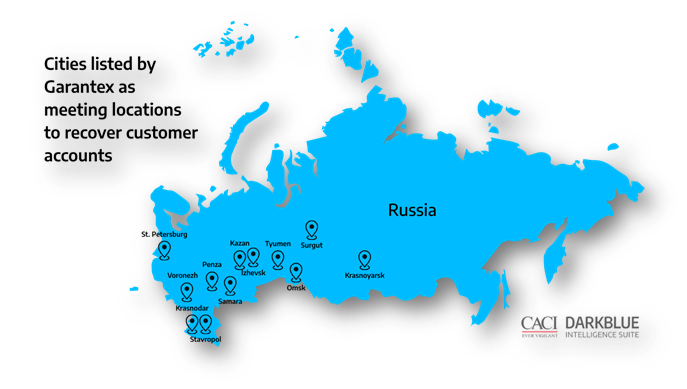
This recovery effort highlights several alarming trends:
- Operational backups: The speed of Garantex’s return suggests that the organization had contingency plans and redundant systems in place long before the crackdown.
- State complicity: The Russian government’s apparent tolerance of these in-person meetings raises serious questions about its role in enabling or even supporting such operations.
- Brazen tactics: The willingness to openly coordinate recovery efforts underlines the confidence criminal enterprises have when operating within jurisdictions that shield them from international law enforcement.
The Russian connection
The resilience of Garantex has fueled speculation about Russian state involvement. Analysts argue that such rapid recovery would be impossible without significant financial backing and political protection. This fits a broader pattern where nation-states like Russia are increasingly seen as complicit—or even active participants—in cybercrime ecosystems targeting Western nations.
CACI analysts have compiled data via the DarkBlue® Intelligence Suite showing that the United States is disproportionately targeted by ransomware attacks and other cybercrimes compared to other countries. For every two attacks on U.S. infrastructure or data systems, the rest of the world combined experiences only one. This disparity underscores how cybercriminal organizations like Garantex are weaponized to destabilize Western economies while enriching themselves.

Caption: Number of ransomware attacks by country so far in 2025, compiled via DarkBlue® data
Implications for global cybersecurity
The saga of Garantex underscores the growing sophistication and resilience of dark web marketplaces and cryptocurrency exchanges involved in illicit activities. It also highlights the challenges faced by international law enforcement agencies in combating these threats:
- Evasion tactics: From frequent wallet migrations to rebranding as new entities, criminal organizations are becoming increasingly adept at evading detection.
- Nation-state support: The involvement—or at least tolerance—of nation-states like Russia complicates enforcement efforts and undermines global cybersecurity.
- Regulatory loopholes: Cryptocurrencies like A7A5 demonstrate how novel financial instruments can be exploited for money laundering on an unprecedented scale.
Conclusion: staying ahead of the curve
The takedown—and subsequent resurrection—of Garantex serves as a stark reminder that traditional enforcement methods are no longer sufficient against modern cybercriminal organizations. To stay ahead of these evolving threats, businesses and governments must adopt advanced intelligence tools capable of monitoring dark web activity and tracing illicit financial flows.
The DarkBlue® Intelligence Suite offers cutting-edge solutions designed for precisely this purpose. Our platform provides actionable insights into emerging cybercrime trends, equipping organizations with the information they need to protect themselves from ransomware attacks, data breaches, and other digital threats. Request a free trial to test out DarkBlue today.
As we’ve seen with Garantex, resilience is not just a trait of criminals—it must also define our response.